FS1SP1131 | Radius on Windows or Linux server | NET and MST (possible NIX) | Assignment Sample
Abstract
Security is vital component for the organization. Establishing security policies is an important responsibility to protect the resources of an organization. enforcing securing principle on each device is difficult to manage. Centralized management of security policies is an efficient solution for an organization. The research will study the centralized security principles and its management. Authentication, Authorization and Accounting are the important security concepts to protect the resources of an organization from the unauthorized access. The security principle allows only the authorized persons into the organization network for accessing only the allowed resources as well as accounting the details of the usage of resources. The research work analyses the security protocol RADIUS and TACACS+. It illustrates the working principle, comparative analysis, merits and demerits of RADIUS and TACACS+, implementation of RADIUS and TACACS+ on Windows server.
Introduction
In an organization, it is responsibility of IT department to manage various routers, firewalls, switches as well as access points throughout network. IT department have to create policies that include who can login into the organization network, what are resources of the organization network can be accessed by the authorised user of the network, how long they use the resources etc. The management of such security policies in each device is complicated task for IT team. Organization requires centralized policy management system for managing their network. Some vendors have implemented standards for implementing such centralized policies. Such policies are vendor specific. AAA is the effective and complete solution for security issues of network (Gibson et al 2017).
The two efficient protocols such as RADIUS and TACACS+ are security protocols that offer Authentication, Authorization and Accounting solution for the organization network. The protocol enables all the network devices can be managed on single platform as well as the protocol available as built in protocols in most of devices (Meyers 2015). The research paper presents the analysis of RADIUS server an TACSCS+ severer for AAA solution. The paper is organizes is as follows: Literature review, Comparative study of RADIUS and TACACS+ server, advantages and disadvantages of RADIUS and TACACS+ server, implementation of RADIUS and TACACS+ server on windows server to secure router, conclusion.
Radius on Windows or Linux server- Literature review
Security is vital component for electronic devices. It plays an important role for securing the sensitive data. Firewalls or anti-virus can be used for providing security for single computer. For networks, it is important to enable security devices as well as security policies for protecting the resources of the network (Besselink et al 2019). Organization network has more valuable and sensitive information. It is the responsibility of the IT team or network administrator of the organization to enable security methods to protect network. Various security protocols exist to achieve secure communication over network. Some of the following protocols are used to provide security such as
P-Point to P-Point P-protocol
Point to point protocol is used to prevent unauthorised users for entering into the dial up connection. it is layer 2 communication protocol which offers point to point communication. The protocol authenticates user name and password. The protocol PPP offers compression, authentication, error detection, Multi-link PPP. It uses L-Link C-Control P-protocol-LCP for establishing as well as configuring link between two end points. N-Network C-Control P-Protocol-NCP used to detect the network protocol used during the connection. The protocol uses the port number 1723 (Li et al 2020).
P-Password A-Authentication P-Protocol-PAP
It is basic as well as simple protocol. The communication using PAP is performed as plaintext including user name as well as password used for authentication. It is insecure way for authenticating. The protocol is heavily vulnerable for man in the middle attack.
C-Challenge H-Handshake A-Authentication P-Protocol –CHAP
It is one of the secure authentication protocol than PAP. When the client needs to authenticate wirh the server, then the server sends challenge message. Then the user has to prove to the server who am I ?. Then the user has to send the password to the server. The protocol converts the password into hash and that will be sent over the network. The server compares that has value with the already stored hash value. When both values are same, then server will allows the user to success the resources on the network.
MS-CHAPv1 and MS-CHAPv2
Microsoft has its own version of CHAP. The protocol is called as MS-CHAP versin1 and version 2. The protocol uses both PPP and PPTP. The protocol MS-CHAP version 2 provides more security than MS-CHAP. It offers two way authentication between client as well as server.it is provides more security and integrity while communicating using the protocol. For dial –up connection, most of the people is still using the protocol MA-CHAP2.
PPP & Authentication, Authorization, and Accounting (AAA) Protocols
Point to point protocol has limitation and issues. The issues has been resolved using the protocol AAA protocol. The authentication provides authentication, authorization as well as accounting services. It is relied on IEEE 802.1x as well as port based N-Network A-Access C-control P-protocol-PNAC. The protocol provides centralized AAA service for their clients. This authentication process is known as R-Remote A-Access S-service-RAS.
The following are the some of the AAA protocols such as
Network administrator performs statistical configuration for network without the concept of AAA. Statistical method for configuring network is inadequate. AAA provides flexibility for network administrators for defining policies for network. The importance of AAA is high due to more number of mobile devices connecting with network, various networks accessing method etc.
Authentication
Authentication is the process of verifying identity of user using user credentials maintained in the database. The user is given user credentials for accessing the network. When the user credentials are matched with the database, then user will be allowed to access the network. Otherwise system will not allow user to access the network.
Network administrator can set various network policies for their network users. For example, site policy allows the user to access the network from on-site location. When the user request network access from remote location, it will allow the user to access the network.
Internet Service Providers may deny network access for the suspended user’s account. Administrator can set limited access for the unknown users of the network. Administrator can provide access to the network according to the user area. This kind of access can be given in the Wi-Fi hot spot (Metz et al 1999).
Authorization
Authorization is the process of determining the permission granted to the user. The Network Access Server is sending request in the form of packet which holds information about user to the RADIUS server. The server processes the request and verifies the user properties for the given request. Server sends user information about the actions allowed or denied to NSA server (Chughtai et al 2019).
Accounting
Accounting is the task of recording the network activities of user. The collected data may include time spent by the user on the network, data received as well as data sent during the session. User activities during session will be sent to RADIUS server through NAS. The summary of traffic is used for billing purpose.
- R-Remote A-Access D-Dial-In U-User S-Service -RADIUS
- Diameter
- T-Terminal A-Access C-Controller A-Access C-Control S-System Pl-Plus -TACACS+
- E-Extensible A-Authentication P-Protocol -EAP
- 802.1X P-Port-based N-Network A-Access C-Control –PNAC
Radius Server
Livingston Enterprises, Inc developed RADIUS protocol as an accounting as well as access server authentication protocol. It has conventions and rules for communication between network devices for the purpose of remote user accounting and authentication. The protocol used by ISP, corporate, providers of cellular network, educational sectors. It provides the following functions such as
- Authentication of users before allowing them into network
- Authorization of user for accessing particular network services
- Accounting user access on those network service
The protocol authenticates remote clients. When the remote try to access the internal network, then Network Access server has send the request to the Radius server to authenticate specific user. The server validates the credentials of the user and sends the replay to the client. When the credentials are valid then it sends the message to the Network Access server to allow the client to access the network. otherwise, it sends the reply that, deny specific client to access the network.
Origin
Merit, non- profit network provider required method for managing dia-in access to different POP –Point of Presence across network in the year 1991. Livingston Enterprise created RADIUS for such reason. Most of the network equipment vendors are utilizing the protocol due to its usability, efficiency and simplicity. The protocol considered as industry standard as well as it positioned as I-Internet E-Engineering T-Task F-Force (IETF) standard.
Beneficiaries
Various business communities are utilizing RADIUS protocol for accounting and authentication purpose. Most widely used customers of RADIUS are
- C-Cellular N-network P-providers-CNP those providing service to millions of users
- Enterprise network with N-Network A-Access C-control-NAC using 802.1 x standard strengthening their network with RADIUS
Advantages of RADIUS
RADIUS client server protocol offers various advantages such as
- Scalable and open solution
- Easily modifiable
- Separation of communication and security processes
- Most security system can adopt RADIUS protocol
- Working on any communication device that has RADIUS client protocol
Free RADIUS
Open source, as well as widely deployed RADIUS server, is FreeRADIUS. It satisfied the authorization, authentication, and accounting need of top companies, Tier 1 Internet service providers, academic sectors, etc. it was initiated in the year 1999 by Miquel van Smoorenburg and Alan DeKok.
Advantages of FreeRADIUS
- Rich features
More authentications can be supported by the FreeRADIUS which includes Extensible Authentication Protocol. It supports virtual servers.
- Modularity
The protocol is easily understandable due to its modular design. It enables easy way for adding and removing modules. Modification of modules does not impact the performance of server.security and usage of memory.
- Scalability
RADIUS server can handle one request per second as well as thousands of requests per second with the simple reconfiguration of setting. Organization has more than 10 million customers are preferring the use of FreeRADIUS for their AAA purpose. Single RADIUS server can satisfy the security need of larger organization.
Security concepts – AAA
AAA is defined as A-Authentication, A-Authorization and A-Accounting. It is an architecture that authenticates user for entering into the network and granting authorization for accessing network resources and accounting activities of users while accessing the network resources. The network architecture without AAA is termed as open architecture which can acceded by any user without any tracking. It is possible to incorporate parts of AAA for an organization. That organization does not need accounting feature they can activate only AA.
Importance of AAA
Network administrator performs statistical configuration for network without the concept of AAA. Statistical method for configuring network is inadequate. AAA provides flexibility for network administrators for defining policies for network. The importance of AAA is high due to more number of mobile devices connecting with network, various networks accessing method etc.
Authentication
Authentication is the process of verifying identity of user using user credentials maintained in the database. The user is given user credentials for accessing the network. When the user credentials are matched with the database, then user will be allowed to access the network. Otherwise system will not allow user to access the network.
Network administrator can set various network policies for their network users. For example, site policy allows the user to access the network from on-site location. When the user request network access from remote location, it will allow the user to access the network.
Internet Service Providers may deny network access for the suspended user’s account. Administrator can set limited access for the unknown users of the network. Administrator can provide access to the network according to the user area. This kind of access can be given in the Wi-Fi hot spot.
Authorization
Authorization is the process of determining the permission granted to the user. The Network Access Server is sending request in the form of packet which holds information about user to the RADIUS server. The server processes the request and verifies the user properties for the given request. Server sends user information about the actions allowed or denied to NSA server.
Accounting
Accounting is the task of recording the network activities of user. The collected data may include time spent by the user on the network, data received as well as data sent during the session. User activities during session will be sent to RADIUS server through NAS. The summary of traffic is used for billing purpose.
ISPs accounting their user’s network access data for billing their customers for every access of network. Corporations use accounting for network monitoring. The detailed information about the network usage is maintained at the NAS such as websites visited by the user, bytes transferred through various protocols such as HTTP, SMTP etc. The detailed information is not forwarded to the RADIUS server.
Network administrator gathers detailed information about the network usage of customer through NetFlow or sFlow. The protocols cannot be integrated with the RADIUS architecture.
Auditing
Auditing is deep analysis of accounting details as well as details from NetFlow or SFlow.
Components of RADIUS system
The protocol RADIUS defines rules and regulations for communication among network devices. It follows client server model. RADIUS client is other called as Network Access Server. RADIUS client sends request to RADIUS server to process request. RADIUS server sends response to the RADIUS client. NAS products have wireless access points as well as dialup equipment to establish network access. Cisco ACS, MS IAS, Juniper, FreeRADIUS, OS Radiator, Steel Belted Radius are the products belong to RADIUS server.
Components
|
Name of the component |
Functions |
Examples |
|
Device/user |
Requesting access for network |
Laptop VOIP A-Asymmetric D-Digital S-Subscriber L-Line -ADSL Modem
|
|
N-Network A-Access S-Server-NSA |
Provides access for devices or users into network |
W-Wireless A-Access P-Point (WAP) Switch Terminator of VPN DSLAM |
|
Authentication server |
Receives request from NAS to authenticate users/device
Return authentication response to NAS Request user as well as configuration details from database or directory optionally
Sends configuration parameters to NAS
Gathers accounting details from NAS
|
FreeRADIUS IAS NPS Radiator ACS
|
|
Data store |
Optional directory and database with user authorisation as well as authentication details, RADIUS server performs communication with data store using LDAP or DB API |
Database (SQL) K-Kerberos S-Service S-Server(KSS) LDAP Directory |
N-Network A-Access S-Server (NAS)
NAS acts as gateway between user and corporation network or wider network. User can get access of network only through NAS. It receives user credentials for accessing the network and passes those credentials for server to further processes such as authentication and authorization.
Authentication
Authentication is the task of verifying user identity for the network. User credentials are one method to verify user authentication. The verification process is known as authentication session. User initiates that session. At the end of the authentication session, the RADIUS server, instructs NAS to allow or deny users for the network access. Security restrictions are enforced by the NAS for the user defined in the RADIUS server. NAS acts as gateway firewall or router for users or devices.
NAS server gathers user’s activities during the session. The summary of activities is forwarded to the RADIUS server.
Various kinds of NAS are switches, W-Wireless A-Access P-Points-WCP, ADSL terminators, D-Digital S-Subscriber L-Line A-Access M-Multiplexers (DSLAM) etc. NAS ensures that only authorized users access the corporate network. The device which authenticates user name and password is known as RADIUS client. It may include web server, FTP server and Unix login server.
RADIUS SERVER
RADIUS server is an application which runs on server. NAS is identical as any other server which gets request from NAS server and process those requests and sends response to NAS server. The data sent to NAS may include authorization policies as well as acknowledgement for receiving accounting information. Single RADIUS server can process more number of requests from different NAS server from various locations. Server can also interact with SQL databases, flat file, directories as well as with other RADIUS servers. The decision can be taken for the access request raised by NAS server is based on the information from various sources.
Once the decision made by RADIUS server that will be forwarded to the NAS client. NAS may enforce security policies based on response. Server is not having any feature to know about whether the response is utilized by the NAS client or not.
In general NAS server is setting security policies for organization. NAS server is the guard for monitoring whether network devices are following the security policies or not.
Policies of the RADIUS server
RADIUS server process NAS client request related with the following conditions such as
- NAS request contents
- Information available for RADIUS server through SQL, flat file as well as LDAP
Server cannot negotiate when the NAS client request more information. It simply receives request from client either sends an acknowledgement or non-acknowledgement. This is the limitation of RADIUS server.
After receiving request from client, it uses policies, local information as well as rules defined by the network administrator in the server. Using that information, server responds for client request. The policies are simple like “accept user with correct user name and password” or it may complex like “allowing basic users for requesting premium resources in the non –premium hours” and so on.
The policies for accessing the network should be designed and deployed by the network administrators. Policies is based on the NAS request content. While setting policies on the server, the policy attributes should be matched with the attributes present in the NAS request. Network administrator uses test login to verify the attributes that represent contents for policies should be matched with the attributes that represent request. Once policies established in the server that will be utilised by the server to make decisions.
The process becomes complex when more than one NAS requests same information in different formats. The formats of NAS client request becomes vary for different NAS client. It is difficult for network administrator to establish policies that adequate for different NAS clients.
Data stores
Data stores are the systems which store huge data as well as retrieve data. The stored data will be useful for decision making procedures. The key difference between data stores and RADIUS server is based on supporting policies as well as authentication. The main role of the data store is authentication is for providing data for RADIUS server. The server can make of the data retrieved from the data store.
RADIUS server can read data as well as write data on database or dictionary while authentication user credentials as well as storing user account details with the database.
RADIUS on windows
Remote Authentication Dian –In User Service (RADIS0 is one of the client server based networking protocol that resides and operates on application layer. The protocol uses RADIUS client and server.
RADIUS client is one of networking device such as router, VPN concentrator, switch that is used for authenticating users. It is also known as Network Access Server.
RADIUS server is running on windows or Linux server which is background process. It is used to maintain user profiles in central database. RADIUS server is used to control network. While user trying to access RADIUS client such as router, switch or VPN concentrator, it sends request to RADIUS server. It performs authorization and authentication for the users those are trying to access the RADIUS client.
RADIUS server provides security for the network on where it resides through security and privacy policies. The working characteristics of the RADIUS server are based on the RADIUS ecosystem. It supports AAA feature such as Authorization, Authentication and Accounting for secure communication over network. Some of the RADIUS server work as proxy for other RADIUS server. It is helpful for setting policies for accessing network as well as establishing security management.
RADIUS server supports various techniques for authenticating users. Initially user initiates authentication process by sending user name and password.
The following are steps for the authentication and Authorization process such as
- User sends user credentials (username, password) to the network such as RADIUS client
- RADUIS client sends request to RADIUS server to authenticate user credentials
- RADIUS client sends access request message to server. The request message includes secret information. User passwords are forwarded to the RADIUS server in the encrypted form.
- RADIUS server validates the Access request of client to ensure whether user is authorised or not. If user is not authorized then server will discard the request message.
- When user is authorized, then server verifies the requested authentication details. When client requested allowed authentication method, server reads credentials of user from message. The credentials are verified with the centralised database. It the credentials are matched then server extracts additional information about the user.
- It verifies whether any access polices or user rights exists for the user in the data base
- If there is no access policy for user, server will send Access-Reject message. The transaction ends. User will be denied to access the system.
- If there is matching policy found in the database, server sends Access-Accept message
- Access-Accept message includes shared secret as well as attribute of filter ID. RADIUS clinet will reject the message if shared secret is not matched
- If shared secret is matched then client reads the value of the attribute filter ID which is string of text. RADIUS client is connecting with user using the filter ID for specific RADIUS group. User are having same filter ID value belong to same RADIUS group. The group enables user categorization based on functionalities such as HR, sales, networking, IT and so on.
- Finally user will get authorization and authentication to access RADIUS client.
RADIUS server accounting
The main purpose of RADIUS server is accounting. It gathers data for billing, monitoring network as well as statistical purpose. RADIUS accounting is independent from RADIUS authorization and authentication.
The basic process for RADIUS accounting is as follows:
- The process will be initiated when the user is granted to access RADIUS server
- RADIUS client sends Accounting -Request to start accounting for RADIUS server. The request includes user ID, session identifier, point of access and network address.
- Client may send additional accounting-request to server during the session. The request packet includes information such as data usage as well as duration of current session. The packet will be transmitted to the RADIUS server for updating the details about the user on current session.
- RADIUS client sends Accounting-Request to the RADIUS server to stop accounting when the user access ends. The requesting packet includes the details relevant to the session of user such as total time spent with the current session, reasons for disconnecting session and so on.
RADIUS server protects organization’s data from being access by unauthorized persons. It enables each user assigned with network permission. RADIUS server can be integrated with existing system without any major changes
TACACS+
Introduction
Security plays vital role for small network to very large network. Without security implementation, network is more vulnerable for the security threats. Without security implementation, users can be assigned with valid IP address simply or getting IP address automatically through D-Dynamic H-Host C-Configuration P-Protocol –DHCP. This process is simple but more vulnerable when the network has sensitive data. Without security implementation, user will have all rights to access all the resources of the network without any restriction. It will lead to dangerous situation for the network (Chen et al 2012).
AAA is the method to protect the network from security threats. The following scenario, depicts that the network without security implementation.
(9tut,2020)
- User will send the authorization details to the router to access the network
- Router validates the authorization details of user and grant permission to access the network
- Gain user sends request to access resources for the network
Importance of AAA for network
- Without security implementation traditional login method leads to insecure environment
- It is vulnerable for brute force attack
- No accountability for users
- Authentication details must be configured on each device or router
- Authentication details must be stored on each local device
- Cannot limit the resources of the network for user
Network with AAA implementation
The following diagram illustrates that, the network is implemented with the security principle such as AAA server.
(9tut, 2020)
- User send request with authentication details to access the network through the router
- Router forwards the request to the AAA server
- AAA server validates the user login details and sends access granted response to user through router
- After completing the authentication process, authorization will begin from the client end
- It send the request to access the resources of the network for example show version
- AAA server validates the authorization details of the user and accepts the request and send response for the request
- If the requested resource is not permitted for the user AAA server send response such as deny
Advantages of AAA
AAA is one the powerful security method. It offers the following advantages such as
- It provides the secure login feature
- Centralized management for user authentication
- Firewalls as well as other security device may be place before the AAA server
- Access controls for user can be specified to accesses the resources of network
- User accounting can be done for analysis of user behaviours as well as accounting
Basics of TACACS+
The management of N-Network A-Access S-Server (NAS) has been increased due to the increasing use of remote access. Centralized administration is required for controlling the user name and password for each user.
T-Terminal A-Access C-Controller A-Access C-Control S-System-TACACS is security protocol for providing centralized validation for users who attempt for gaining access to router or NAS. The recent version of TACACS is the TACACS+. The protocol provides authorization, authentication and accounting services.
It provides detailed accounting as well as flexile administration over the process Authorization, Authentication and Accounting. The protocol TACACS+ allows client to request detailed access control and also allows the process of TACACS+ for responding to each component of that request. The protocol uses T-Transmission C-Control P-Protocol –TCP for transportation. Security can be achieved in TACACS+ through encrypting the traffic between process and NAS. Encryption is based on secret key that known only to the client as well as TACACS+ process.
Components of TACACS+
NAS
N-Network A-Access S-Server-NAS, the device which provides access for the user to the network. It offers network connections to single user, network or sub network or interconnected networks. With reference to TACASC+, NAS is the E-Series router.
Process-TACACS+
A software or program which runs on security server that delivers AAA services using the protocol TACACS+. It processes the request of NAS for Authentication, Authorization and Accounting. While processing the request of NAS, it can also respond to NAS with request for additional details such as password.
TACACS+-server
The server which runs the TACACS+ process is known as TACACS+ server.
Authentication, Authorization and Accounting
The protocol TACACS+ is used to perform an effective communication for AAA between NAS server as well as central server.
Authentication
Authentication is the task of ensuring that the user is granted to access the network or not. The permitted user can be identified through the use of user name and password. Authentication is used to prevent intruders into the network.
Authorization
Authorization is the task of assigning permission to user for accessing the resources. When the user is authenticated to allow to the network then user can access the resources based on their assigned permission. Network manager limit the access control on the resources for the users.
Accounting
User details can be recorded in the accounting process. It tracks what actions performed by the users and when it performed. It can be used for audit trail as well as billing. It is independent process from authorization and authentication.
TACACS+
It is security protocol that allows NAS for communicating with authentication server for determining the user has the access for the network. The protocol is developed by CISCO which replaces the earlier two standard protocols such as TACACS as well as XTACACS.
The services of TACACS+ server are maintained in database on TACACS+ daemon running on windows 2000/NT as well as UNIX. Cisco’s servers supporting TACACS+ which include CiscoSecure UNIX, Cisco access Registrar, CiscoSecure ACS for Windows.
TACACS+ supports AAA architecture through separating authentication, authorization and accounting. It gives flexibility for using another services such as Kerberos for authentication, and TACACS+ is used for authorization and accounting (Kim 2004).
It is connection oriented TCP protocol between client and servers. It uses TCP port 49 . TCP ACK is used to provide acknowledge for the receiving request. The TCP process is using the RST packets for providing indication of failed authentication server. TCP keepalives is used for watching failed servers as well as facilitate failover between multiple connected authentication servers. Scaling as well as adaptation is better for TCP for growing congested networks.
TACACS+ also provides support for bidirectional response/challenge similar to CHAP between two NAS. It supports PPP as well as SLIP protocols. It also gives support for the following protocols such as
- N-Novell A-Asynchronous S-Services I-Interface -NASI
- X.25 PAD connection
- Net BIOS Frame Protocol Control protocol
- A-AppleTalk R-Remote A-Access P-protocol (ARAP)
Encryption
The protocol encrypts data payload of packet excluding header of TACACS+. The body of the packet remains encrypted for the debugging purpose. For achieving more security, the entire body of packets will be encrypted. Header file indicates whether the body is encrypted or not.
Features of TACACS+
- Protocol developed by CISCO for the purpose AAA
- It can be used between devices and access control server
- Protocol TCP used for transmission
- Protocol uses the port TCP 49
- The packets of AAA communication are encrypted between the devices and ACS server
- It provides more granular control
- If offers efficient accounting support
Working principle of TACACS+ protocol
The protocol enables communication between NAS server and Authentication server. In TACACS+, N-Network A-Access S-Server (NAS) or N-Network A-Access D-Device (NAD) is the client. When the user enters into the network, NAS send request to the TACACS+ server to provide user name prompt for the user through the message Continue. User will enter username then NAS server send request to TACACS+ server to provide password prompt for the user (Rybaczyk 2000). The user will enter password, then NAS send the password to the TACACS+ server.
The server will send either one of the following response to NAS such as
- TACACS+ server will send ACCEPT when the user credentials are valid
- TACACS+ server will send REJECT when the user credentials are not valid
- If there is no connection in between TACACS+ server and NAS server, TACACS+ will send ERROR message
- ACCEPT message includes attributes that represents the services those are allowed for the user.
The protocol uses TCP port 49 for the communication between TACASC+ server and TACACS+ client. For example, TACACS+ client is switch as well as ACS/ISE is TACACS+ server.
The protocol encrypts the payload/packet. It separates the process of authorization, authentication and accounting. The protocol is used for device administration.
Session flow for the process Authentication
- Client or switch initiates the session through sending the message START. It indicates that the request is coming for the AAA server or ACS server
- AAA server or ACS server sends the message REPLY. It instructs the client to provide the user name
- Client sends the message CONTINUE with user name to server
- Server sends the message REPLY to client to provide password
- Client sends the message CONTINUE with password to server
- Server sends the message FINAL REPLY to client with the indication of any one of the following
- Accept (it represents authentication success as well as authorization process will proceed)
- Reject (it indicates authentication failed)
- Error (there is no connection between server and client or an error in the method of authentication)
- Continue (it has more information for authentication to get success)
Session flow for Authorization & Accounting
Two messages are used to perform Authorization as well as Accounting:
- Request ----->Request server for the user to access resources (commands send through Command Line Interface)
- Response ----->Response will be given by the server for granting permission for user to access the resources or denying permission to access the resources
TACACS+
The protocol is an extended version of TACACS. It forwards the user name as well as password to the centralized security server.
The topology of TACACS+ is depicted below
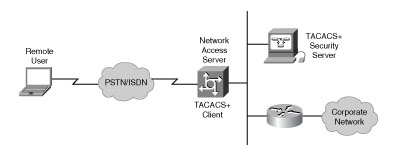
(CISCOPRESS, 2020)
The protocol TACACS+ has the following features such as
- Reliable TCP packets for data communication
The protocol TACACS+ uses the T-Transmission C-Control P-protocol –TCP as communication protocol between security server as well as remote client. The protocol support the architecture AAA
- Encrypted link
The payload of the TCP packets are encrypted to provide more security as well as the encrypted data will be stored in the security database. The protocol supports CHAP, PAP as well as MS-CHAP authentication protocol for achieving security. It is useful for both WAN and LAN security.
- Dialup security support through S-Serial L-Line I-Internet P-Protocol -SLIP, PPP, and ARA
The protocol SLIP is direct connections and modems over TCP/IP that allows one computer for connecting with another computer or network. PPP is the security protocol which is powerful than SLIP protocol which supports multiple protocols through built-in security. The protocol ARA is used for Macintosh users to get direct access for information as well as resources at remote Apple Talk site.
It supports the addresses TN3270 as well as X.121 are also used with X.25. It provides the following benefits such as supporting for auto command, support for call-back and access list for each user can be assigned in the authorization phase.
Login Authentication for administrative
Every login authentication of NAS server is verified with the process of TACACS+. There are three packets used for authentication process such as
- Start
- Continue
- Reply
The packets start and continue will be sent by the user whereas reply packet will be sent by the server or TACACS+ process.
The protocol TACACS+ establishes TCP connection between TACACS+ host as well as server and staring sending the start packets from the client. TACACA+ process will send the reply packets with either granting, denying access for the user, errors or challenges.
The protocol may challenge the user for providing user name as well as password and passcode. The requested information will be entered by the TACACS+ client with the continue packet over existing connection. The server TACACS+ will send the reply. When authentication process completes connection will be closed. It allows only three login retries.
Privilege authentication
The process is used to determine whether user allowed for using commands at specific privilege level. This kind of authentication is similar to login authentication except that use can use one authentication attempt. Access denial is indicated with the empty reply. The authentication process enables default command for setting privilege authentication.
Login authorization
The following authorization commands are used for login authorization with TACACS+ server such as
- aaa authorization
- aaa authorization config-commands and
- authorization
Accounting
User activities are recoded through the process of accounting. The service that enables to create audit trail of user execution session as well as C-Command L-Line I-interface (CLI) C-commands those are executed in the user session. It can be used to track user with their CLI connects as well as disconnects, when configuration model entered as well as exited and which of the configuration as well as commands executed.
The accounting method can be defines with the following details such as
- service type
it indicates the type of information is being recorded
- name
The name represents the unique accounting method within the type of service
- mode of accounting
The mode indicates type of accounting record to be generated in auditing process.
- method
It indicates the protocol to send accounting records for security server.
List of method
The specification of configuration defines the way NAS performs the accounting services of AAA. Different method lists as well as names are used to configure service type. Various service types may use different name of method list. TACACS+ accounting is disabled until defining the method list of accounting.
There are two kind of method list in accounting such as
- Default
Names list is not assigned when the configuration used by lines and controls. Default method list can be activated for each service type by enabling through the accounting.
- named
While assigning named list, it will override the default named list. Named list will be assigned to specific line, console or group of lines.
Service type
It indicates the type of the service delivered by TACACS+ accounting service
- Exec
It presents the details about terminal session of Exec such as L-Local A-Area T-Transport –LAT, telnet, as well as rlogin on NAS.
- Commands
It presents the details about Exec mode CLI commands for particular level of privilege that are executed on NAS. The records of accounting are generated for the commands run by the users, C-command L-line I-Interface scripts as well as macros (Ventura 2001).
Mode of accounting
The records of accounting are used for tracking the actions of users as well as resources used by the users. The records can be used for the management of network, auditing as well as billing purposes. There are two modes for modes for accounting such as
- Start – stop
The accounting record start is generating before the beginning of the process as well as stop accounting record is generating after the successful completion of the process. The type of the service Exec only can use the mode
- Stop only
Stop accounting record is generating after the successful completion of the process. The service type command use this type of mode.
The accounting data of TACACS+ includes the following fields such as attribute/field, location as well as description. Some of the attributes of accounting data are as follows:
major_version, type, minor_version, flags, pri-level, user,port, rem-addr and so on.
Most of network device manufacturers support TACACS+ such as Adtran, Avocent/Cyclades, Citrix, Alcatel/Lucent, Arbor, Edgewater, Aruba, Blade Networks, EMC, BlueCat Networks, Extreme, Blue Coat, IBM, Brocade/Foundry, Netgear, Cisco/Linksys, Dell, Enterasys, Ericsson/Redback, Nortel, Fortinet, Fujitsu, Juniper/Netscreen, HP/3Com, Huawei, Palo Alto Networks, Riverstone, Radware, and Samsung
Access control server is essential for providing centralized management for authorization, authentication and accounting. The communication between server and client will be carried out using the protocols such as RADIUS and TACACS+.
RADIUS vs TACACS+
Introduction
RADIUS protocol was designed for authenticating log dialup remote users for the network. TACACS+ is used for the purpose of administrator access to the network devices router and switches. The name of the protocol explains their usage such a RADIUS - Remote Access Dial-In User Service and TACACS+ T-Terminal A-Access C-Controller A-Access C-Control S-Service P-Plus. Generally, the protocol RADIUS is sued to authenticate remote user for the network whereas TACCACS+ is used to authenticate network devices such as switch or router.
RADIUS protocol cannot log the commands given by the administrator. It is used to log only the start, stop as well as interim record of the session. When two or more administrators log on to the network, the protocol cannot distinguish which command is given by which administrator.
The functional difference among RADIUS and TACACS+ protocol is that there is clear separation of authorization functionalities in TACACS+. RADIUS has the combination of authentication and authorization functionalities.
The issues of the RADIUS protocol can be resolved with the use of TACACS+ protocol. It is the standard security protocol developed by department of defence, U.S. later the protocol enhanced by CISCO. It separates the functionality authorization from authentication, which provides more flexibility as well as granular access control on the device access with commands. While entering the commands by the user, it will transmit to the centralized server for authorization purpose. Each command of the user is validated in the TACACS+ server against the list of authorised commands (Kizza 2009).
It can define policies based on type of device, user, time as well as location. TACACS+ is used to for locally configured users, groups defined in Active Directory as well as LDAP for controlling access to the devices in the network. The protocol enables S-Single S-sign O-on-SSO that simplifies management, increases security as well as it will be easy for users.
RADIUS is mainly designed for providing AAA services for subscriber whereas TACACS+ mainly implemented for providing AAA services for network administrator. RADIUS can also be used by small networks where authorization is not required as well as it should be homogenous network. when the network is heterogeneous nature and authorization is required means TACACS+ is the better option.
RADIUS protocol is using the UDP for Transmission. It does not have implicit hand shaking method to provide reliability, intefrity and odering.
The difference between RADIUS and TACACS+ is illustrated in the below diagram
Supporting vendors
Most of network device manufacturers support TACACS+ such as Adtran, Avocent/Cyclades, Citrix, Alcatel/Lucent, Arbor, Edgewater, Aruba, Blade Networks, EMC, BlueCat Networks, Extreme, Blue Coat, IBM, Brocade/Foundry, Netgear, Cisco/Linksys, Dell, Enterasys, Ericsson/Redback, Nortel, Fortinet, Fujitsu, Juniper/Netscreen, HP/3Com, Huawei, Palo Alto Networks, Riverstone, Radware, and Samsung
Access control server is essential for providing centralized management for authorization, authentication and accounting. The communication between server and client will be carried out using the protocols such as RADIUS and TACACS+.
Deployment
It is not good idea for deploying both protocols on one server. Even though, both protocols are implemented to provide AAA services, resources utilized by the protocols different, licensing of the protocols is proving more expenses. While deploying the two protocols on same server, it will reduce the security of the network.
In fully trusted network, TACACS+ servers can be deployed. The network does not have any direct communication from the untrusted network or semi structured network. RADIUS server can be deployed on semi –trusted network. TACACS+ will be used for internal administrative logins. While deploying TACACS+ server on semi-structured network with windows domain controller, it needs to open many ports for SMB, LDAP, NTP and DNS. While deploying TACACS+ server on tructed network, there is need to open only one port such as TCP 49.
TACACS+ server should be installed very close for the user database. Both user database as well as TACACS+ server should be installed on the same server. While using Active directory as database, it is better to install TACACS+ on domain controller. It will increase the performance. while installing user database and TACACS+ server on different location will create connection issues, problems related with DNS, time discrepancies and so on.
Licensing
Two security protocols are different in licencing. The protocol RADIUS needs expensive licensing and it is more complex protocol. The complexity of the protocol is based on more than 40 RFCs written on RADIUS. In TACACS+ has only one RFC. RADIUS does not provide value for administrator access to network devices.
TACACS+
The protocol Terminal Access Controller Access Control System (TACACS+) developed by CISCO. It enables communication between Cisco server and client. The communication is carried out using the port TCP 49.
RADIUS
Remote Access Dial In User Service –RADIUS is standard protocol which is open that can be used by any vendor for establishing communication between client and ACS server. RADIUS can be used when one of the client or server not belong to the CISCO community. The protocol uses the port numbers such as 1812 for the purpose of Authentication as well as 1813 for accounting.
RADIUS vs TACACS+
The working principle is same on both of the protocols such as RADIUS and TACACS+ for authentication process. The communication process starts from the client or N-Network A-Access D-Device (NAD). Client sends request for authentication to the server (RADIUS or TACACS+). Server sends the user name and password prompt to the client for providing user name and password. The authentication details for forwarded to the server to authenticate client. Server will send replay to the client in the form of access-accept or access-reject. When the authentication details entered by the client are valid then server will send access-accept otherwise it will send access-reject message to the client.
The protocols are working different on authorization as well as accounting. Authorization as well as accounting is combined in RADIUS.
|
S.No |
Factors |
TACACS+ |
RADIUS |
|
1 |
Protocol |
proprietary protocol of CISCO |
Open standard protocol |
|
2 |
Transmission protocol |
Transmission Control Protocol |
User Datagram Protocol |
|
3 |
Ports |
TCP ports 40 |
Authorization & Authentication uses UDP port 1812, Accounting uses UDP port 1813 |
|
4 |
Services |
Separation of Authentication process, Authorization process and Accounting process |
Both Authentication as well as Authorization combined in RADIUS |
|
5 |
Encryption |
Entire packets will be encrypted |
Password will be encrypted where as other details such as user name and accounting details are not encrypted |
|
6 |
Entity |
Used with A-Access C-Control S-Server-ACS |
Used with I-Identity S-Service E-Engine |
|
7 |
Supporting granular control |
Supports particular command for authorizatin |
No support for external authorization |
|
8 |
Support multiple protocol |
Support for multiple protocol |
No support for multiple protocol |
|
9 |
Purpose |
Device administration |
Network access |
Advantages (TACACS+ vs RADIUS)
- Protocol TACACS+ uses Transmission control protocol which is reliable than the UDP protocol
- It offers more control for the authorization commands, the protocol RADIUS do not support external authorization commands
- It achieves more security than RADIUS in which whole packets will be encrypted. Whereas, in RADIUS only password will be encrypted
Advantages (RADIUS vs TACACS+)
- The protocol can be used for all vendors including Cisco due to its open standard nature
- It provides more accounting support than TACACS+
Installing RADIUS server in windows
Initially server manager application will be opened. Click on “Mange” from the menu then select “Add Roles and Features”.

Next “Add roles and Features Wizard” window will be opened. From the window server role---à Network policy and Access services will be selected.
In the “Add Roles and Features Wizard” click on Add Features.
Again, From the “Add Roles and Features Wizard” window, select sub menuà “Role service” from the menu Network policy and Access control. Check the option “Network policy service”.
Select confirmation option from the from the Add roles and services wizard. Then click install
Now Radius server installation process completes on windows 2012.
Creating authorized users
The next step after installation is to create authorization users for authentication using RADIUS. Creating user groups is the task of creating user accounts on the RADIUS server for authorization purpose. The application Active Directory users and computers will be opened from the domain controller. New user group will be created inside the Users folder with Users--àNew-àGroup.
The new group will be created with the name “RADIUS-USERS”
The users in the new group will be allowed to access the server. Now, two user accounts will be created. The following step will be followed to create user such as
UsersàNew-àUser
The following will create user for the RADIUS server
From the window click “Next” to add the “User “ as Member of Radius server”.
Next, creating second user with the name “Goku”
The created users are allowed by the RADIUS server.
Adding client devices
Network policy server application will be opened from the Radius server. Authorizing Radius server on Active Directory Database is required. Right click-àNPS(Local)--à Register Server in Active Directory
Click “Ok” for confirmation
Configuring Radius Clients
Radius clients are devices that are requesting authentication services for the Radius server. Click Radius client (Folder)-àNew
The above screen indicates that, client configured for allowing Cisco switch to access Radius server by providing the following details such as friendly name, IP address, shared secret.
Another client device will be configured to connect with the RADIUS server. Now, the desktop is configured as RADIUS client to the RADIUS server.
Now Radius client configuration completed
Configuring Network polic
Network policy will be created to allow authentication. Right click -à Network policy (Folder)à new
Specifying Name then click --àok
Adding user groups for the Radius server
Select user group then click add
Click the option access granted
Check the option unencrypted authentication in the New Network policy window
Verifying configuration summary of Radius server than click finish
Radius server configuration finished
Authentication process
To perform authentication process, NTRadPing software is running on the device. The device should be the Radius client for the Radius server.
The above mentioned user is authenticated user for the Radius server. User account created in the active directory.
RADIUS
The protocol carries information related with authentication, authorization as well as accounting between client and server. Client is the Network Access Server –NAS or switch or Router which authenticates its link with the shared Authentication server.

Network access server is the Radius Client that communicates with the Radius server to authenticate devices. Radius or NAS receives request from the devices on the network to access the network. The device will verify the authentication details of the requested device with the Radius server. The device NAS is the interface for backbone and POTS or ISDN. The device is receiving call from the hosts that want access the backbone through dialup services. NAS device is located at the ISP’s point for providing internet access for their customers.
Network Access server-NAS manages network access for remote resources. NAS is otherwise called as media access gateway or R-remote A-access S-server-RAS which manages the resources centrally and provides access to the border network like internet.
Internet service
One of the major services of NAS is for serving as gateway for protecting remote resources. Internet service providers providing internet services through modem like devices like cable or DSL that use NAS devices accepts P-point to P-point P-protocol (PPP), P-Point- P-Point T-tunnelling P-protocol (PPTP), P-Point-to-P-Point P-Protocol over E-Ethernet (PPPE) for authentication, authorization as well as accounting purposes.
The NAS resides between Internet backbone as well as local ISP providers for authenticating remote users to access the internet. The system receives dial up calls from remote host to access the internet. It verifies the user credentials with the centralized database and allows the user to access the internet when the authentication details are valid for the user.
Communication application
NAS is act as remote access gateway for the remote services such as VoIP as well as web conferencing. To provide the VoIP as well as web conferencing services, NAS will verify the IP address or phone number instead of verifying the user name and password. When the phone number is valid then NAS allow the call to complete.
NAS also support for network management, optimization processes like recourse management on network, load balancing and user session.
In the enterprise network, wireless Access point or switch act as NAS device for ensuring that the corporate network should be accessed only by the authorized users. Carriers use D-digital S-subscriber L-line A-access M-multiplexers –DSLAM or A-asymmetric D-digital S-subscriber L-line ADSL terminators are also can act as NAS device to authenticate users as well as maintaining account information of user for billing purpose.
VPN services
VPN-Virtual Private Network connects remote users with private network. In an organization, remote employees can connect with the organization network more securely through VPN. It is helpful for organization to enable their employees working from remote place and accessing the organization resources.
VPN network includes NAS combined with client software. When the user tries to access the organization network, NAS device authenticates the remote employee.
Security is serious challenge in networks. Server credentials are one of the targets for the attackers. Security protocol RADIUS provides authentication, Authorization as well as accounting services to provide more security for network.
WiFi security using RADIUS server
Wi-Fi network provides wireless communication among the devices on the network. In an organization, wireless Access Points or routers are providing access to the employees to access the resources of the network. The users are allowed into the network when the user provides valid user name and password. The credentials of the Wi-Fi connection can be shared with various users. When the credentials of the Wi-Fi connectivity is leaked, it provides chances for unknown users to access the network, It can be avoided through the RADIUS protocol.
In RADIUS architecture, each user of the network is assigned with user credentials. The user credentials are synchronized with the active directory/LDAP. Radius may be implemented as on-premise server using the commercial RADIUS server or open source server. Many of the network devices as well as server OS has built in RADIUS software.
RADIUS and TACACS+
Advantages of RADIUS
More security benefits
RADIUS allows authentication of each user with unique user credentials which provides more security for the network
No password management
Each user of network is assigned with unique authentication. The protocol does not follow password shared techniques among users. It does not require password change management. No need for the he administrator to change the password of the network frequently.
Central authentication management
User credentials as well as system credential are maintained at the centralized server for perfroming AAA.
Efficient tool for large network
The tool provides support for large number of user through the centralized server technique. It controls the network from the unauthorized users. It limits who is use the network, what resources should be accessed by the user and maintains the details such as when they access resources (Lu et al 2013).
Disadvantages of Radius
On-prem implementation
While implementing RADIUS server as on-premise device, it is difficult to manage. It is time consuming process due to regular upkeep as well as monitoring. The management of on-premise Radius server is more frustrating and intensive.
Initial Radius server setup
It is difficult for the IT administrator to set up Radius server, when the organization is already equipped with some of the security services such as Active Directory etc.
More configurations
Initial set up of Radius server need more configurations. It incurred for various compatibility issues. It has very complex process.
RADIUS protocol cannot log the commands given by the administrator. It is used to log only the start, stop as well as interim record of the session. When two or more administrators log on to the network, the protocol cannot distinguish which command is given by which administrator.
The functional difference among RADIUS and TACACS+ protocol is that there is clear separation of authorization functionalities in TACACS+. RADIUS has the combination of authentication and authorization functionalities.
The issues of the RADIUS protocol can be resolved with the use of TACACS+ protocol. It is the standard security protocol developed by department of defence, U.S. later the protocol enhanced by CISCO. It separates the functionality authorization from authentication, which provides more flexibility as well as granular access control on the device access with commands. While entering the commands by the user, it will transmit to the centralized server for authorization purpose. Each command of the user is validated in the TACACS+ server against the list of authorised commands.
It can define policies based on type of device, user, time as well as location. TACACS+ is used to for locally configured users, groups defined in Active Directory as well as LDAP for controlling access to the devices in the network. The protocol enables S-Single S-sign O-on-SSO that simplifies management, increases security as well as it will be easy for users (Tubun et al 2019).
Installing and configuring TACSCA+ server on windows server 2012 & Cisco router
The protocol T-Terminal A-Access C-Controller A-Access C-Control S-System –TACACS offers centralized validation for the users. The protocol verifies the authentication details of the each remote user with the centralized server database to allow access for the router. The protocol enable communication between the authentication server or router as well as remote access server for validating the user credentials. The protocol TACACS+ provide the solution for security issues in network through the AAA services.
Authentication
Authentication is the process of verifying identity of user using user credentials maintained in the database. The user is given user credentials for accessing the network. When the user credentials are matched with the database, then user will be allowed to access the network. Otherwise system will not allow user to access the network (Posso et al 2019).
Network administrator can set various network policies for their network users. For example, site policy allows the user to access the network from on-site location. When the user request network access from remote location, it will allow the user to access the network.
Internet Service Providers may deny network access for the suspended user’s account. Administrator can set limited access for the unknown users of the network. Administrator can provide access to the network according to the user area. This kind of access can be given in the Wi-Fi hot spot.
Authorization
Authorization is the process of determining the permission granted to the user. The Network Access Server is sending request in the form of packet which holds information about user to the RADIUS server. The server processes the request and verifies the user properties for the given request. Server sends user information about the actions allowed or denied to NSA server.
Accounting
Accounting is the task of recording the network activities of user. The collected data may include time spent by the user on the network, data received as well as data sent during the session. User activities during session will be sent to RADIUS server through NAS. The summary of traffic is used for billing purpose.
ISPs accounting their user’s network access data for billing their customers for every access of network. Corporations use accounting for network monitoring. The detailed information about the network usage is maintained at the NAS such as websites visited by the user, bytes transferred through various protocols such as HTTP, SMTP etc.
The topology of the TACACS+ server is illustrated in the figure
Free version of TACACS+ can be downloaded from the source http://www.tacacs.net/download.asp
TACACS+ can be installed on the windows server 2012 with the IP address 192.168.5.3
During installation, it will ask user to enter secret
After installing the TACACS+ ready only attributes of the file from the config folder will be changed
Integration of TACACS+ server and Active directory
Active directory users will be created allowed by the CICCO router.
Implementation
RADIUS on windows server
Assigning Host name and IP address
Configuration of RADIUS server
Informing to Router RA that RADIUS server will be used for Authentication
Testing telnet access from PC
Implementation of RADIUS and TACACS+ usingCISCO
Enable and configuration of Router
Configuring TACACS+ server
Configuring AAA model
authentication
Conclusion
Security is vital component for organization. Establishing security policies is an important responsibility to protect the resources of an organization. Enforcing securing principle on each device is difficult to manage. Centralized management of security policies is an efficient solution for an organization. The research will study the centralized security principles and its management. Authentication, Authorization and Accounting are the important security concepts to protect the resources of an organization from the unauthorized access. The security principle allows only the authorized persons into the organization network for accessing only the allowed resources as well as accounting the details of the usage of resources. In an organization, it is responsibility of IT department to manage various routers, firewalls, switches as well as access points throughout network. IT department have to create policies that include who can login into the organization network, what are resources of the organization network can be accessed by the authorised user of the network, how long they use the resources etc. The management of such security policies in each device is complicated task for IT team. The research work analyses the security protocol RADIUS and TACACS+. It illustrated the working principle, comparative analysis, merits and demerits of RADIUS and TACACS+, implementation of RADIUS and TACACS+ on Windows server.
RADIUS security protocol has some of the limitation like unreliable due to UDP communication protocol, no separate functionalities of authentication and authorization and so on. TACACS+ provides more security for the organization resources. In fully trusted network, TACACS+ servers can be deployed. The network does not have any direct communication from the untrusted network or semi structured network. RADIUS server can be deployed on semi –trusted network. TACACS+ will be used for internal administrative logins. While deploying TACACS+ server on semi-structured network with windows domain controller, it needs to open many ports for SMB, LDAP, NTP and DNS. While deploying TACACS+ server on trusted network, there is need to open only one port such as TCP 49.
References
- Gibson, D. (2017). CompTIA SECURITY+ Get Certified Get Ahead SY0401 Study Guide. Virginia Beach, VA: YCDA, LLC
- Meyers, M. (2015). All in One CompTIA Network+ Certification Exam N10-006. McGraw-Hill Education: New York, NY.
- Besselink, N. J., Westgeest, A. A. A., Klaasen, R., Gamala, M., Van Woerkom, J. M., Tekstra, J.& Van Laar, J. M. (2019). Novel optical spectral transmission (OST)-guided versus conventionally disease activity-guided treatment: study protocol of a randomized clinical trial on guidance of a treat-to-target strategy for early rheumatoid arthritis. Trials, 20(1), 226.
- Li, D., Deyu, H. U., & Chen, J. (2020). U.S. Patent Application No. 16/711,579.
- Chughtai, F., UlAmin, R., Malik, A. S., & Saeed, N. (2019). Performance Analysis of Microsoft Network Policy Server and FreeRADIUS Authentication Systems in 802.1 x based Secured Wired Ethernet using PEAP. INTERNATIONAL ARAB JOURNAL OF INFORMATION TECHNOLOGY, 16(5), 862-870.
- Metz, C. (1999). AAA protocols: authentication, authorization, and accounting for the Internet. IEEE Internet Computing, 3(6), 75-79.
- Ventura, H. (2001). Diameter: Next generations AAA protocol.
- Kizza, J. M. (2009). Computer Network Security Protocols. In A Guide to Computer Network Security (pp. 365-395). Springer, London.
- Lu, Y. Y., Yang, Y., Yin, Z. H., & Yu, B. C. (2013). The research and design of campus network security development on Cisco AAA certification. In Applied Mechanics and Materials (Vol. 411, pp. 662-666). Trans Tech Publications Ltd.
- Tubun, A., & Anabell, G. (2019). Análisis de prestaciones de los protocolos de autenticación remota RADIUS y TACACS+ en infraestructura de comunicaciones corporativas (Bachelor's thesis, Escuela Superior Politécnica de Chimborazo).
- Posso, R., & Criollo-C, S. (2019, April). Analysis of Authentication Failures in the Enterprise. In World Conference on Information Systems and Technologies (pp. 911-920). Springer, Cham.
